Cybersecurity is a growing concern for organizations all over the world. A single attack can lead to thousands or even millions in losses, and cybercriminals continue to come up with more sophisticated methods of attack. Ransomware and malware threats are some of the most common types of cyberattacks.
Let’s take a look at how big of a risk these threats are right now and dive into what the average small to mid-sized business can do to protect itself from an attack.
Ransomware and Malware – What’s the Difference?
Ransomware and malware are sometimes used interchangeably, but they aren’t the same thing. It’s important to know the difference to ensure you have the right protocols and cyber protection in place to protect your business.
Malware
Malware is a blanket term that refers to all types of malicious code or files that are used to damage a user’s device or network.
- Trojan horses, worms, spyware, and viruses are all types of malware.
- Hackers send malware through emails, USB drives, and software installations. You can also open your computer or your network up to malware simply from browsing the internet.
- Once malware is on your computer or network, it can cause a number of problems ranging from slowing down performance to a loss of control over your data.
Ransomware
Ransomware is one type of malware, and it’s generally the most difficult one to protect against. A cyber attacker will use ransomware specifically to stop you from accessing your system or your data until you pay them a fee. It’s essentially malware designed to hold your device or network for ransom.
- Ransomware is primarily delivered via phishing emails. A tainted email will have a malicious attachment or a deceptive link that takes you to an infected website if you click on it. Cyber attackers can also send ransomware in an instant message.
- With this type of threat, an attacker may lock you out of your system or encrypt your files so you can’t access them.
How Big of a Threat Are They?
Robust antivirus software and email encryption can help to protect against many malware threats. Ransomware, however, is a massive business threat. It doesn’t matter if you have a global enterprise or a small company – all organizations are vulnerable.
To give you an idea of the size of the problem, look at these numbers:
- In 2021, global ransomware damages are expected to cost organizations $20 billion – that’s 57 times more than the cost of damages in 2015.
- By the end of 2021, a business will be attacked by ransomware every 11 seconds.
- From 2019 to 2020, there was a 62 percent increase in the number of global ransomware attacks.
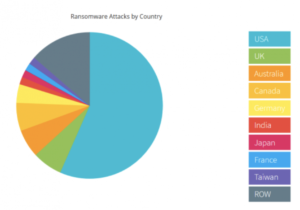
- Last year, more than half of all successful ransomware attacks occurred in the US.
Wondering what happens in a typical ransomware attack? Often, cyber attackers will lock your system and demand payment, usually in Bitcoin. Other times they will take down your IT system or wreak havoc in other ways. Because you can’t access your data when you’re under attack, you may also have to deal with days of downtime.
No matter what the specifics are, ransomware attacks are always difficult and often very expensive. Your business may have to pay for:
- A ransomware recovery IT team to get your company back online and to ensure the IT infrastructure is secure
- A digital forensics team to identify exactly what happened
- A public relations firm to help you with any reputational damage caused by the attack
- The actual ransom – you can hire a ransomware negotiator to try and bring down the cost of the ransom and to manage the transaction on your behalf
How to Protect Against Malware and Ransomware Threats
While the threat of these cyberattacks is unnerving, there are many tools a business can use to mitigate risk and keep your systems protected.
- Real-time backup. With real-time file backups, you can restore your files to any point you need to from the cloud. This enables fast recovery from ransomware attacks. It may save you from having to pay a ransom and reduce business downtime. Make sure your cloud backup solution includes advanced antimalware and antivirus software.
- Employee training. Phishing emails are the main point of entry for ransomware attacks. All it takes is one individual unknowingly clicking on a malicious link or file attachment to put your business at risk. Make sure all of your employees are aware of the threat of ransomware attacks. They should know how to spot a phishing email and what to do if they think they may have clicked on a malicious link. Also, in general, all employees should be cautious of any email or instant message that they aren’t familiar with.
- Advanced email protection. Because emails are ground zero for cyberattacks, it’s worth it to consider an advanced email protection solution. Ideally, your email protection comes with anti-phishing and anti-spoofing protection to help filter out external threats, malicious link protection, and outbound scanning. This helps to prevent malware from spreading if an employee clicks on a phishing link.
NTELogic offers comprehensive, multi-layered email protection for SMBs, as well as secure backup and file management. Our expert team is also happy to talk to you about how Email Protection, ShareSync, and other Intermedia solutions can help protect your business from ransomware and malware threats. Contact us today to learn more.

